Companies are now seeking scalable and robust applications, which can meet both years of functional performance and user expectations. That’s when full-stack Node.js development comes into play, uniting the power of frontend and backend within a single environment. It allows developers to build faster and smarter while creating applications to remain adaptable as the business continues to grow.
In this way, constructing end-to-end solutions is more fluid and intelligent. With cohesive databases, APIs, and user interfaces integrating and interfacing, developers can automate some of the hassle proactively. Understanding full-stack Node.js ultimately gives developers an advantage to think forward as technology grows and gives organizations tangible opportunities to grow with applications that perform and scale easily. So, let’s dive in to know how this expertise truly makes a difference.
Want to build an advanced application without compromising performance? At Mindpath, our full-stack development services will help you provide the best solutions, handling both front-end and back-end with efficiency.
Understanding the Fundamentals of Full-Stack Development
Full-stack development means developing on the front end and back end of a web application. The front end refers to all the things that the user responds to and interacts with, such as buttons, layouts, designs, etc. The back end refers to all of the things that run in the background, like databases, servers, etc., and all the logic that makes it run smoothly, working together.
A full-stack developer has the capability to deal with both sides. They are capable of building UX and the technology that serves the app. This gives them agile skills that allow them to build comprehensive applications entirely from front to back.
Understanding the Basics of Node.js
Node.js is a platform that allows you to run JavaScript code in a JavaScript runtime outside of the browser. It is built on Google’s V8 engine, which is extremely fast and built to be efficient. Node.js allows developers to write server-side applications using the same exact language as for the front end, making development and management easier and smoother.
An advantage of Node.js is that it operates asynchronously, which allows tasks to not have to wait for one another to complete, meaning that applications can handle multiple requests at once. Because of this, the use of full-stack Node.js is quickly becoming a good choice when building scalable, real-time, and modern applications.
The success of using Node.js in full-stack development depends on hiring the best developer. Discover the key Factors to Consider while Hiring Node.js Developers.
Why is Node.js Important for Full-Stack Development?
Utilizing Node.js full-stack technology is an impressive approach to developing a complete web application. Here are reasons that Node.js is a valuable technology option in the full-stack.
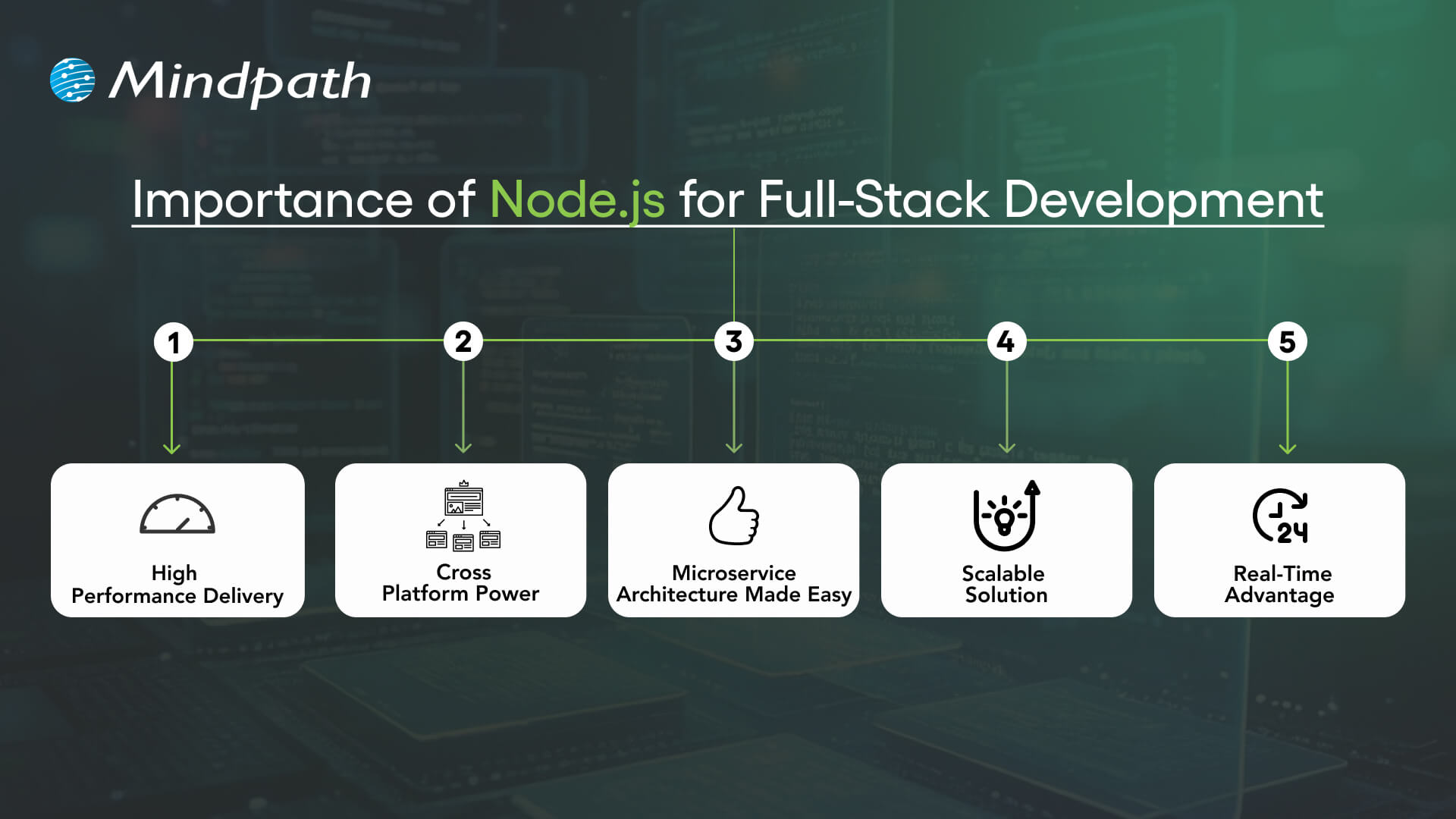
1. High Performance Delivery
Node.js utilizes a non-blocking I/O hardware model that can handle hundreds or even thousands of requests simultaneously, providing faster response times and greater user-specific.
2. Cross-Platform Power
With the Node.js full stack, developers can write mobile and desktop apps to run on Windows, macOS, Linux, and more. By relying on a single JavaScript code base, developers can save time and effort writing for multiple platforms.
3. Microservice Architecture Made Easy
Full-stack Node allows users to break one larger application down to multiple smaller independent services using infrastructure that is easier to work with. This approach lets developers build faster, stay flexible, and rely on proven solutions.
4. Scalable Solution
Full-stack Node.js is used by major players like Walmart, Uber, and Trello to handle millions of users. It helps to lower load time significantly, and it ensures your applications will scale seamlessly, as your demands increase.
5. Real-Time Advantage
When it comes to applications that leverage chat, live streaming, food delivery, or payments, Node.js full-stack is the way to go. It seamlessly provides real-time updates to keep the user engaged and connected.
Also Read: Full-stack Development for Web Projects
Key Steps to Use Node.js in Full-Stack Development
A full-stack Node.js developer is involved in both the front end and the back end of web application development and will work to build complete web applications. Below is a synopsis of the primary steps to utilize Node.js in full-stack development that is easy and productive.
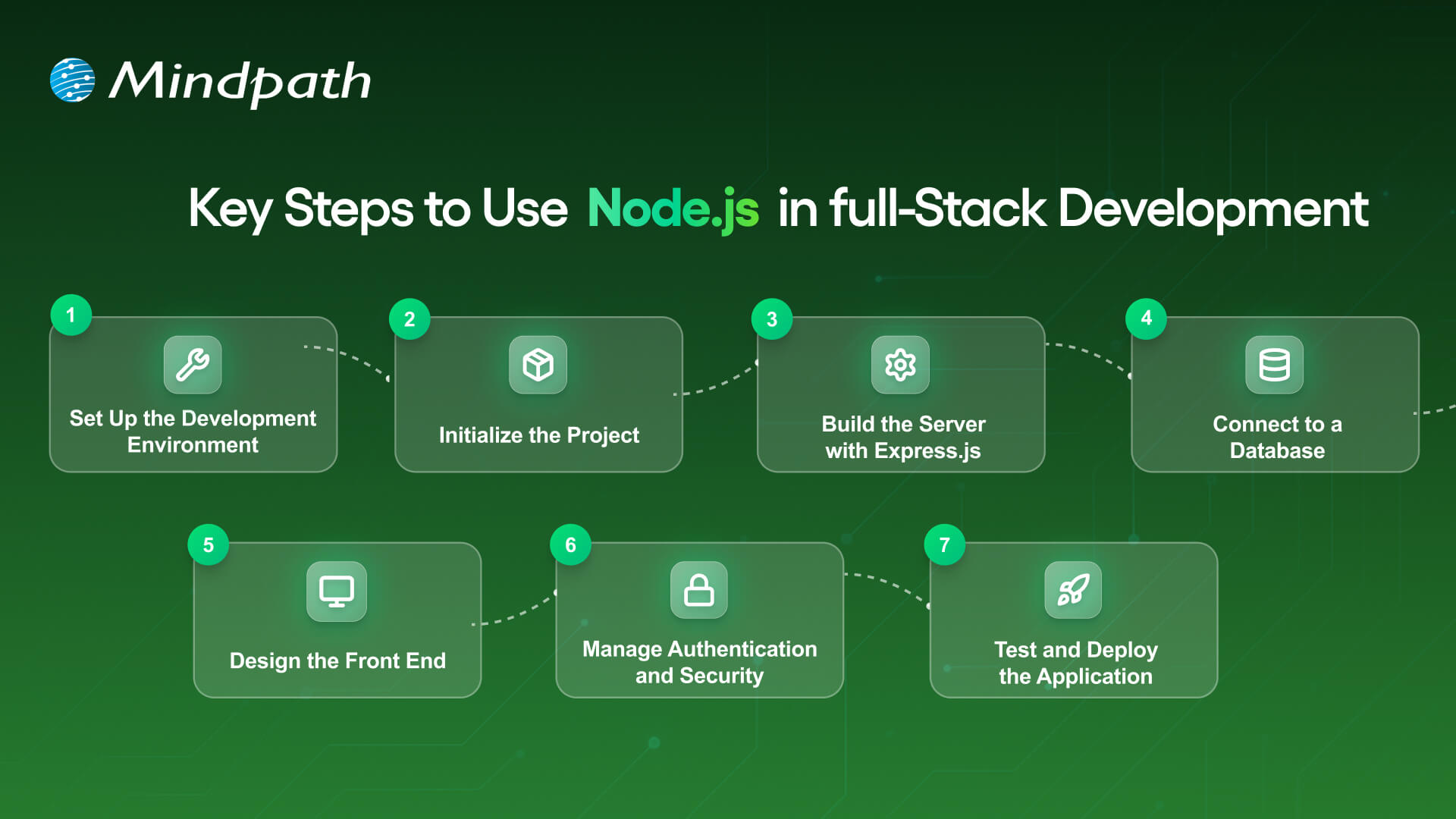
1. Set Up the Development Environment
To begin your application-building experience, you will need to install Node.js and npm (Node Package Manager). These tools will allow you to execute JavaScript beyond the browser, and they will also help manage libraries with ease. Verify the setup by checking versions with simple commands in your terminal.
2. Initialize the Project
Make a new folder for your app, and use ‘npm init’ to create a ‘package.json’ file. A package.json file holds important information, such as your project name, dependencies, and scripts. It will serve as the basis for managing everything in your project.
3. Build the Server with Express.js
Install Express.js so you’ll be able to set up the backend server and handle all of the different routes. Express.js makes handling requests, responses and APIs supposedly easy. This step will ensure the backend runs appropriately with the frontend.
Must Read: Full-stack development trends
4. Connect to a Database
Based on your needs for this project, select a database like MongoDB or PostgreSQL. This should be paired with a Node.js library like Mongoose or Sequelize, which will allow you to connect to and perform both read and write operations on your data. At this point, you will have the ability for your application to persist and retrieve your data.
5. Design the Front-End
Build the front-end using a library such as React, Angular, or Vue. You can link the front-end through RESTful APIs or GraphQL to your Node.js back end. At this point, players will finish the bridge for a Full-stack Node.js application.
6. Manage Authentication and Security
Use libraries like Passport.js or JWT to add secure login and registration. Secure necessary paths so that any authorized user can get to those routes. You should always consider security in any Full-stack Node.js application.
7. Test and Deploy the Application
Create unit and integration tests to ensure that your application does what you intended. Deploy the application to cloud hosting solutions like Google Cloud, AWS, or Heroku. To utilize your Full-stack Node.js application’s performance tool on different scales, you should monitor its performance!
Looking to integrate AI in your Node.js projects? Explore our Ultimate Guide to Node.js Libraries for AI Integration to discover the most effective libraries for building smart, scalable, and future-ready applications.
Ready to Unlock the Power of Full-Stack Node.js?
Full-stack Node.js has proved to be a smart choice for building scalable, high-performing, and real-time applications. It unites front-end and back-end seamlessly, helping developers create complete solutions with speed and flexibility. With its ability to handle microservices, cross-platform apps, and real-time updates, it has become an essential technology for modern web development.
At Mindpath, we provide expert full-stack development services designed to match your business goals. Our skilled Node.js developers bring deep technical knowledge and practical experience to build secure, scalable, and user-friendly applications. If you are looking to transform your digital ideas into reality, hiring a Node.js expert from our team ensures growth and lasting impact.












